Compliance Challenges
- International customers’ foremost requirement is for adequacy of systems and process controls with security of personal data
- Regulatory Risks:
- Stringent non-compliance consequences
- Industry specific regulatory requirements
- Timebound reviews and reporting deadlines
1. Systems and Organization Controls – SOC 1 & SOC 2 – Reviews
Features of these reviews are:
| Why SOC Reviews? |
It is a ‘must have’ for all the organisations having international clients or aspiring growth in international markets. Benefits of SOC Reviews are visible in the form of increased customer confidence and consequential business growth. Considering the importance of SOC Reviews, it is even mandatory for organizations providing outsourced services to their clients listed on US Stock Exchanges. |
|
|
Nature of Review
|
Compliance with Systems & Organisation Controls (SOC 1 & SOC 2) under SSAE18 Standard for Attestation Services issued by AICPA. This review includes controls at organisation, systems and process level governing its people-process-technology aspects.> |
|
| Type of Review | SOC 1 | SOC 2 |
| Applicability |
Validation of controls around processes and systems at Service Organization that affects financial reporting of their client organization. Example of such services are Payroll Processing, Collection Services, Accounting Activities etc. |
Validation of controls at Entity level, Process level and Systems level at the Service Organisation that does not affect financial reporting of the client organisation, but the stakeholders are concerned about Confidentiality, Integrity, Availability, Privacy and Trust Principles Examples of such services are Software Development, SaaS Services, Reward Program Management etc. |
| Set of Controls |
Controls are customized to specific nature of activities performed by respective Service Organisation and systems implemented.
|
Set of 62 controls are standardised for all entities based on COSO Internal Control Practices and covering confidentiality, integrity of data processing, availability, Privacy and Trust Principles |
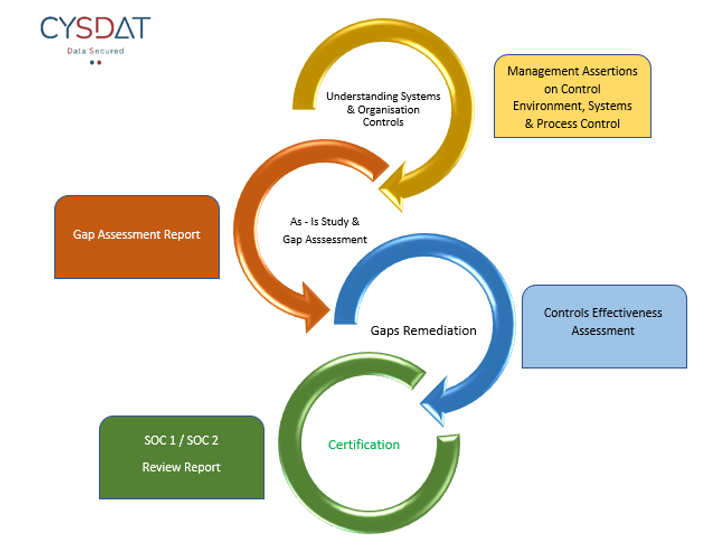
Our approach to SOC Reviews Engagement Flow covers following steps
Our team has vast experience of assistance to many organizations on SOC 1 & SOC 2 readiness leading to their successful certification and maintenance of required controls. This experience covers wide range of outsourced services; including:
• Payroll Processing
• Accounting & Vendor Payments Outsourcing
• Collections & Receivables Management
• Software Development
• SaaS Services through Cloud Hosted Applications
• Reward Program Management
2. Regulatory Compliances
Various guidelines are issued by the respective industry Regulator, some of these are following highlights of our services related to the Cyber Security Reviews as per various Regulatory requirements:
- Information Technology Framework for NBFC – by Reserve Bank of India (RBI)
- Cyber Security Guidelines for Insurance Companies and Intermediaries – by Insurance Regulations & Development Authority (IRDA)
- Cyber Security & Cyber Resilience Guidelines for Mutual Funds / Asset management Companies – by Securities & Exchange Board of India (SEBI)

Compliances for NBFCs
RBI has issued directions pertaining to adoption of Information Technology Framework implementation for NBFCs
Applicability (RBI Circular: RBI/DNBS/2016-17/53 Master Direction DNBS. PPD. No. 04/66.15.001/2016-17 dated June 08, 2017). The following is scope defined as per the Circular”
- Mandatory for all NBFCs with AUM more than Rs. 500 Cr. to follow the directions of Section “A”
- Recommendatory for others NBFCs – “Section A & B”.
- To ensure adequate controls in the following areas as per section A & B of the above referred circular:
- IT Governance,
- IT Policy,
- Information & Cyber Security,
- IT Operations,
- IS Audit,
- Business Continuity Planning and IT Services Outsourcing.
-
Cert-IN directions u/s. 70B (6), of IT Act, 2000, circular no. 20(3)/ 2022-CERT-In related to reporting on information security incident reporting.
-
RBI guidelines on Digital Lending, dated: 02/09/2022, no. RBI/2022-23/111 – areas related to information security will be covered in the audit.
-
VAPT is carried out for the assets identified by the Management
Our approach to conduct IS Audit for NBFCs includes following steps:
Understanding IT
Environment
- Review of Information Security Policy & Procedures
- Understanding of IT Infrastructure and IT Operations
- Review previous reports for tracking closure of reported issues
IS Audit
Controls Testing
- Review of controls around information confidentiality, integrity and availability aspects for each of the area of scope of work.
Gaps
Identification
- Identify the control gaps based on review of sample of records and evidences for the respective area vis- à-vis Information Security Policy, Procedures and RBI IT Framework Circular and VAPT.
Management
Discussions
- Discuss the control gaps identified during the review with the IT Team/ Management to check existence of any compensating controls and assess the likely impact of issues identified
Recommendations &
Reporting
- Submit draft reports covering the scope to IT Team with recommendations to remediate/ avoid control gaps
- Obtain Management Responses towards issues and recommendations
- Submit final reports to Sr. Management

Compliances for
Insurance Companies &
Insurance Intermediaries
I.
Insurance sector regulator, IRDA, has issued guidelines for cyber security audits in October 2022, reference: IRDAI/GA&HR/GDL/MISC/JII /10/2022 dated: October 11, 2022
This circular has a detailed list of over 300 specific controls covering various areas of cyber security and these are benchmarked to the global cyber security framework of National Institute of Standards and Technology (NIST). This framework covers cyber security controls in following areas:
- Identify (ID)
- Protect (PR)
- Detect (DE)
- +Respond (RS)
- Recover (RC)

- Insurers (Life, Non-Life, Health, Re-insurer and Foreign Re-Insurance Branches)
- Brokers
- Corporate Agents
- Web Aggregators
- Third Party Administrators
- Insurance Marketing Firms (IMFs)
8. Insurance Information Bureau (IIB)
9. Insurance Agents
10. Insurance Self Networking Portal (ISNP)
11. Motor Dealers
12. Common Service Centres (CSC)
13. Point of Sale (POS)

II.
IRDA issued amendment to investment regulations for insurance companies in 2013. These amended provisions required implementation of investment risk management systems and process by insurance companies. These systems and processes are to be reviewed and certified by a Chartered Accountant as per the procedure laid town in the Technical Guide issued by the ICAI.
The audit covers following areas listed in the ICAI Guide:
- Annexure A – Key Regulatory issues related to registration
- Annexure B – SOP related to Investment Operations & Risk Management Process & Systems
- Annexure C – IT Systems supporting Investment Operations
- Annexure D – Application Controls and Interface Systems

Entity Environment
- Understanding the IT Environment
- Review of Policy and Procedures

Risk Identification
- Risk Identification
- Testing of Information Security Controls
- Identification of Gaps

Reporting
- Gap Assessment Report
- Management Discussions
- Assistance in Gap Remediation
- Follow-up and Re-testing
- Management Reporting
Our team has successfully audited insurance companies and intermediaries as per IRDA circulars on information and cyber security.